15 WordPress security best practices

WordPress is the world’s most popular CMS mainly because of its ease of use. While that’s convenient for users, it also offers many targets for hackers trying to gain unauthorized access, steal user information, and sabotage websites. That’s when WordPress security best practices come in to protect your site.
Securing a WordPress site requires taking a series of security measures that close off common security gaps that attackers exploit to break into computer systems.
This article will explore 15 WordPress security best practices every owner should apply on their site to keep it secure.
Why is securing WordPress necessary?
Cybercrime is big business for hackers. The World Economic Forum estimates that in 2021 global cybercrime costs reached $6 trillion, which could rise to $10 trillion annually in 2025.
WordPress security is important because:
- Security breaches are expensive and can dent a company’s financial state.
- A widespread lack of cybersecurity affects users emotionally and financially by exposing their data and making them vulnerable to identity theft, loss of credit card information, and more.
- Security breaches affect a company’s reputation, eventually leading to financial issues.
- Users expect websites and computer systems to be secure.
- Unsecured websites may run into legal trouble, depending on the jurisdiction.
- Secure websites receive an SEO boost on search engines.
With that context in mind, let’s move on to the security best practices that will help you avoid common threats and vulnerabilities.
15 WordPress security best practices
The following are the minimum actions you should take to increase the security of your WordPress site, divided into categories.
Installations and updates
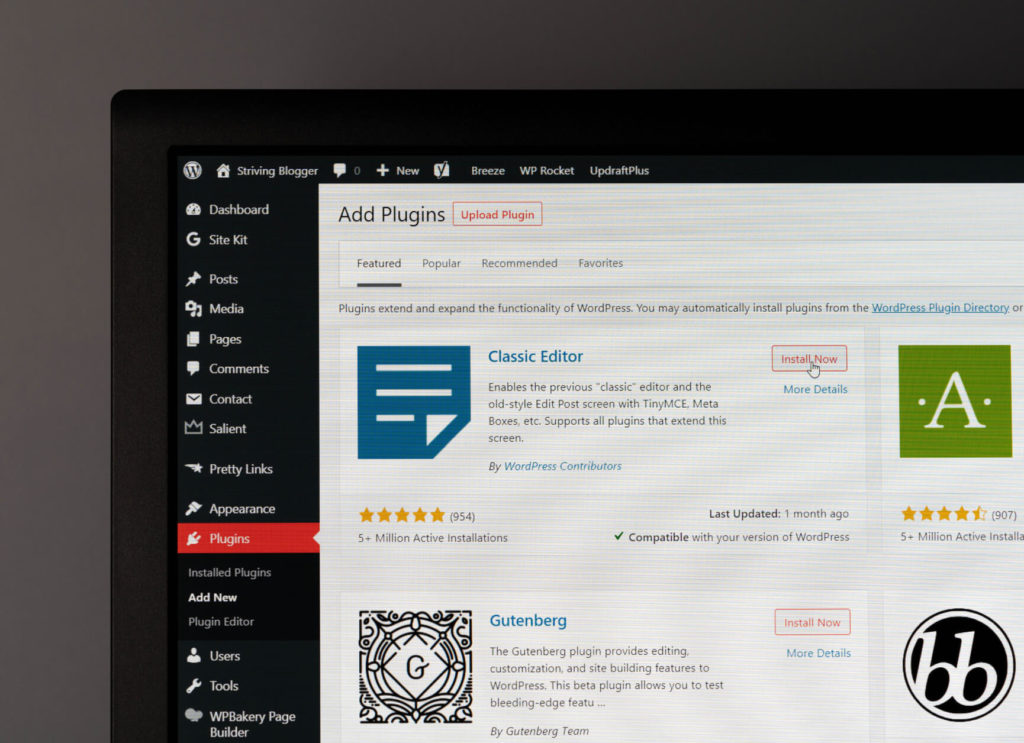
Constantly update your WordPress core
Updates are the most essential of WordPress security best practices. That’s because security threats, vulnerabilities, and solutions are constantly changing. What works today may not work a few years from now, and WordPress developers know it. That’s why they regularly review their code in search of security vulnerabilities.
Updating your core improves security, fixes known bugs, and improves performance for your entire site. Always back up your site before updating its components, including your core files.
Constantly update your PHP version
Like the WordPress core file, you should keep your PHP version updated. PHP versions generally last two to three years before being updated. After that, the next-to-latest version will receive security updates for about two more years, and then it’ll no longer be supported.
Using outdated PHP versions is a significant security risk and a performance liability for your site.
Only install secure WordPress themes and plugins
A plugin or theme can’t stay 100% secure forever. Hackers are always exploring code and experimenting with new attacks, so developers need to offer continuous support.
In the case of plugins, visit the WPScan Vulnerability Database. It lists known security vulnerabilities in plugins. If you see the plugin you plan to install is part of the list, check whether it’s been updated since the vulnerability became publicly known. If not, you may be better off without it.
For themes, check whether:
- It receives constant updates.
- Developers offer direct support.
- Developers are transparent about who’s involved in the process.
- You can find unbiased reviews on their official website.
- It’s popular and well-known.
These points apply to plugins, too.
Finally, only download plugins and themes from trusted sources like the official WordPress plugin repository.
Passwords and login

Use strong, unique passwords on all accounts related to WordPress
Avoid short passwords with common words in them, and avoid reusing passwords for multiple accounts. Follow these guidelines when creating unique passwords for all team members.
- Use long (12-20 characters) complex passwords that combine upper and lowercase letters, numbers, and special characters, such as “*” and “/.”
- Consider creating rules for the words in passwords. For example, you can demand that words be truncated halfway or that vowels are removed (“honey” turns into “hny”) to avoid using predictable letter combinations.
- Avoid common, everyday words and predictable patterns, such as a common word followed by four numbers.
- Don’t use “a” or “1” as the password’s first character.
- Use unique passwords for all accounts associated with your WordPress site.
- Consider using a password manager to keep up with all these complex, unique passwords.
Use plugins to limit the number of failed login attempts
WordPress allows infinite failed login attempts to your site by default. A hacker can keep trying to crack your passwords until they succeed.
Explore plugins that temporarily prevent IP addresses from trying to access your admin dashboard if they fail a certain amount of times in a row (like 3, 5, or 10 times). The most popular plugin that limits login attempts is Limit Login Attempts Reloaded.
Enable multi-factor authentication on every possible account
Multiple-factor authentication is a form of access control that allows access only after the user has provided two or more identity proofs. Often, only two proofs are required: two-factor authentication.
Some popular plugins enabling two-factor authentication include Shield WordPress Security, Google Authenticator – Two Factor Authentication (2FA), and Duo Two-Factor Authentication.
Explore ways to add two-factor authentication to other accounts associated with your WordPress site, like your cPanel and email addresses, using your website’s domain.
Restrict user permissions only to what’s necessary for their roles
Restricting user permissions is essential because if a hacker were to crack an account’s credentials, the damage they can do to that account is limited to what the account has permission to do. Strictly establishing user permissions minimizes potential entry points.
You can modify file permissions by using an FTP client like FileZilla and right-clicking on files and folders. You’ll get a list of permissions for each type of user, which you can modify.
Create logs to record every action users take while logged in
Monitoring user activity means creating an automated log (which pages they opened, which files they downloaded, etc.). Determining which users are legitimate and which are bots or compromised accounts is necessary.
Plugins like Sucuri, WP Security Audit Log, Simple History, and ActivityLog create user activity logs.
Change your default login URL
Your site’s login URL is “www.yourwebsite123.com/wp-admin/” by default. This is convenient for admins but also for attackers trying to brute force their way into your dashboard.
You should change your login URL to a less predictable location. By hiding it from users outside the admin circle, you take a significant step toward securing your site. Read our guide on using the WPS Hide Login plugin to change your login URL’s location.
Scans, cleanups, and site-wide security

Host your website with a secure hosting provider
The services your web host offers to play a role in website security. When choosing or changing hosts, consider whether they provide the following services:
- Securing and restricting access to confidential information.
- Easily backing up and restoring your website.
- Scanning for malware.
- Preventing denial-of-service attacks.
- Offering maximum uptime.
Choose the web host that offers the best balance of security measures.
Install a plugin that runs regular malware scans
Malware scanners explore your website’s files to:
- Identify and eliminate malware.
- Prevent malware from spreading to user computers and stealing user data.
- Protecting databases from injection attacks.
Some of WordPress’s most popular malware scanners are Sucuri, Wordfence, and iThemes security.
Enable SSL/HTTPS so visitors can securely connect to your site
SSL certificates are a necessity for safe web browsing. Their benefits include the following:
- Protecting login information.
- Domain, organization, and extended validations. A Certificate Authority (an organization that manages SSL certificates) validates that your website is run by the people it claims to be run by.
- SEO ranking boost.
More authoritative and validated SSL certificates cost money. However, less authoritative certificates can be obtained for free while still providing a secure connection to visitors. Some popular plugins offering free SSL certificates include WP LetsEncrypt, Really Simple SSL, and WP Force SSL.
Use file integrity checks to detect breaches and potential backdoors
Also known as file changes scanning and file changes monitoring, file integrity checkers scan a file’s so-called “fingerprint,” a cryptographic hash that acts as an identifier for a file’s change history. If the contents of the file change, like when you rewrite code or modify a text file, the hash changes, too.
File integrity checkers notify administrators when a file’s hash changes. These changes can be benign and desired but may also indicate malicious action. For example, an attacker can modify a .php file to create a backdoor to your site, an unauthorized entry point.
Website File Changes Monitor is the most popular integrity checker in WordPress.
Use a web application firewall to block access and filter malicious activity
Web application firewalls (WAFs) act at the application layer, where users interact with apps such as websites. WAFs offer the following benefits:
- Filtering, monitoring, and blocking malicious HTTPS traffic attempting to enter web applications.
- Preventing unauthorized data from leaving the application.
- Creating an application profile to understand data patterns, typical requests, URLs, and allowed values and data types. App profiles make recognizing illegal, abnormal, and malicious requests easier.
- Providing content delivery networks (CDNs). CDNs improve website load times, user experience, and SEO metrics.
- Protection from cross-site scripting and SQL injection attacks are two of the most prevalent security threats.
- Flexible and easily deployed from the cloud or as a local software/hardware installation.
Popular WordPress WAF plugins include Sucuri, WebARX, Wordfence, MalCare, and Cloudflare.
Backups

Regularly back up your website in external locations (not only on the server it’s hosted in)
Backing up your website is making a copy of all the files that make your WordPress website possible, including the core installation files, plugins, themes, and databases.
You can back up websites manually, with a plugin, or with your web host. Using your web host is the most convenient option, but remember to keep multiple backups at multiple locations.
If all your backups are on the same server as your website, any critical failure that brings down your site may also bring down your backups, essentially wiping them along with your live site. For a complete guide to backing up your site, read our article about WordPress backups.
Common vulnerabilities and threats
Attackers are constantly probing the WordPress environment to exploit weak spots. These are the most common types of WordPress security threats:
- Backdoors: software that bypasses login mechanisms to gain unauthorized access to a site.
- Hacktools (hacking tools): programs created to crack or break security systems.
- SEO Spam: once your site’s been broken into, SEO spammers fill your website with links to external sites. Generally, it’s a way for a malicious third party to inflate their SEO rankings by building a catalog of (unwilling) backlinks.
- Phishing: through emails or other messages, hackers pose as legitimate brands and companies to get victims to share personal data such as credit card numbers.
- Defacements: once a site’s been broken into, hackers replace the original website with a new one, sometimes in an attempt to ask for ransom in exchange for restoring the original website.
- Mailers: emails containing malicious attachments that, when downloaded, launch an attack on the device.
- Droppers: malware designed to install viruses, backdoors, etc., into the devices that interact with it.
WordPress security best practices like the ones we’ve explored in this article are designed to block common breaching attempts using methods like these.
Conclusion
Applying these WordPress security best practices will help you proactively avoid widespread security threats like SEO spam, backdoors, and cross-site scripting.
Taking care of WordPress security is a serious matter that can take time to get the hang of, but once you do, enforcing it will save you time, resources, and a lot of headaches.
If you found this article helpful, read our blog for more WordPress insights, guides, and tricks.
Related Articles

WordPress 101 / 8 min read
WordPress 101 / 8 min read
How to audit a WordPress website’s security?
WordPress, being the most popular content management system, attracts a fair amount of malicious attention. To prevent yours from falling victim to a cyberattack, you should periodically audit your WordPress…
Read More
WordPress Security / 10 min read
WordPress Security / 10 min read
Why Is Your WordPress Site “Not Secure”? What You Need to Know
In July 2018, Google Chrome started flagging sites without an SSL certificate as “not secure.” Any website still using HTTP instead of HTTPS to exchange information with users has been…
Read More
How to... / 7 min read
How to... / 7 min read
WordPress CSRF attacks: what they are and how to prevent them?
WordPress CSRF (cross-site request forgery) attacks are one of the most common security vulnerabilities plugin, theme, and website developers have to account for. A dedicated hacker can take over admin…
Read More
How to... / 8 min read
How to... / 8 min read
WordPress SEO spam: what is it and how to prevent it?
WordPress SEO spam is one of the most common security threats for websites using this CMS. It can get your website labeled deceptive, cause your users to suffer scams, and…
Read More
WordPress Security / 7 min read
WordPress Security / 7 min read
WordPress supply chain attacks: what are they and how to prevent them?
WordPress is the most popular content management system, attracting many hackers wanting to exploit such a rich ecosystem for their benefit. WordPress supply chain attacks are one of the methods…
Read More